In the context of the increasing popularity of mobile office, the USB tethering function of mobile phones brings great convenience to us. However, at the same time, it also brings many potential risks to the data security of computers. It is crucial to understand these risks and take effective measures to disable this function to ensure data security.
I. Functions of USB Tethering
Simply put, USB tethering is a function that shares the mobile phone’s network connection with other devices such as computers through a USB data cable. When we are in an environment without Wi-Fi or wired network, we only need a USB cable to connect the mobile phone and the computer, and turn on the USB tethering function of the mobile phone. Then the computer can access the Internet through the mobile phone’s mobile data (4G, 5G) or the connected Wi-Fi network. Compared with Wi-Fi hotspot sharing, this method has a more stable connection, less interference, and a relatively higher data transmission rate. Moreover, while sharing the network, data can be transmitted between the mobile phone and the computer through the data cable, which can be said to kill two birds with one stone. For example, when it is necessary to handle urgent work tasks outdoors and there is no available network around, USB tethering can come in handy, allowing the computer to quickly connect to the network and carry out work.
II. Risks to Computer Data Security
(I) Network Boundary Breakthrough
For confidential computers or computers in internal private networks, they should maintain strict physical isolation from the Internet. However, once connected via mobile phone USB tethering, it is like opening a gap in the originally closed network boundary, allowing the computer to directly access the public network. This undoubtedly provides an opportunity for external malicious attackers, who can easily bypass the originally complex network protection system, directly enter the internal network, and steal or tamper with data in the computer.
(2) Malware Propagation
As a device connected to the public network, mobile phones are faced with many threats from malware in daily use. When a mobile phone is connected to a computer via USB and shares the network, the hidden malware on the mobile phone is very likely to infect the computer through this opportunity. Once these malware run on the computer, they may perform various dangerous operations, such as stealing users’ login accounts, passwords and other sensitive information, transmitting important files in the computer to external servers, and even controlling the computer’s hardware devices, causing serious damage to the computer system. Moreover, since computers are often in an office network environment, malware may further spread to the entire office network using the computer as a springboard, leading to larger – scale data security accidents.
(3) Risk of Data Leakage
Malicious users can use the connection of mobile phone USB tethering to actively transmit confidential files, trade secrets and other important data in the computer to the outside through the mobile phone network without the computer user’s knowledge. In addition, some malware may automatically scan files in the computer in the background, screen out sensitive data and quietly send them out through the mobile phone network. Because data transmission is carried out through the mobile phone as an intermediate device, it becomes more difficult to track the source of data leakage, which greatly increases the risk and loss of data leakage.
III. Methods and Disadvantages of Disabling USB Tethering
(I) BIOS/UEFI Settings
When the computer starts, press a specific key (the key may vary for different brand computers, commonly F2, F10, Delete, etc.) to enter the BIOS/UEFI settings interface. In the BIOS/UEFI menu, find the settings related to USB, which are usually located under the “Advanced” or “Security” menu. Here, set “USB Controller”, “USB Support” or similar options to “Disabled”. Save the settings and exit BIOS/UEFI. After the computer restarts, all USB ports will be disabled, including the ports used to connect mobile phones to implement USB tethering.
This method has significant disadvantages. It disables all USB ports, which means that common USB devices such as USB mice, keyboards, and U disks cannot be used normally, seriously affecting daily work and operations. Users need to prepare additional non – USB interface devices for replacement, bringing great inconvenience.
(2) Device Manager Disabling
Right – click the “Start” button and select “Device Manager”; or enter “Device Manager” in the search bar and open it. In Device Manager, find “USB Controllers” or “Universal Serial Bus Controllers”. After expanding this option, right – click the USB Root Hub you want to disable and select “Disable Device”. After performing this operation, all USB devices connected to this controller will be unavailable, including the mobile phone connection used for USB tethering.
The disadvantage of this method is that it can only disable the controller corresponding to the currently connected USB device. If you replace the USB port to insert a new device or re – enable the disabled controller, the device can still be recognized and used. It cannot fundamentally and long – term prevent the activation of the USB tethering function, and the protection effect is limited and unstable.
(3) Group Policy Settings
For Windows systems, run “gpedit.msc” to open the Group Policy Editor. In the Group Policy Editor, expand “Computer Configuration” → “Administrative Templates” → “System” → “Device Installation” → “Device Installation Restrictions” in sequence. Find the option “Prevent installation of devices not described by other policy settings” or “Prevent installation of removable devices”, double – click to open it, select “Enabled”, and then click “OK”. In this way, you can prevent the computer from installing new USB devices, thereby preventing mobile phones from connecting to the computer through the USB tethering function.
However, this method only takes effect on devices that comply with group policy rules. For some devices that have undergone special driver modifications or can bypass group policy detection, it may not be able to completely prevent their connection, resulting in certain security vulnerabilities. Moreover, the steps of group policy settings are relatively complex. For non – professional users, the operation is difficult, and it is easy to set errors, leading to abnormalities in other functions.
IV. GiliSoft USB Lock Helps Solve the Problem
From the disadvantages of the above three methods, it can be seen that when disabling USB tethering, they either affect the normal use of other devices, or have poor protection effects, or are complicated to operate. As a professional third – party software, GiliSoft USB Lock shows significant advantages of being convenient, simple and having no side effects in disabling USB tethering.
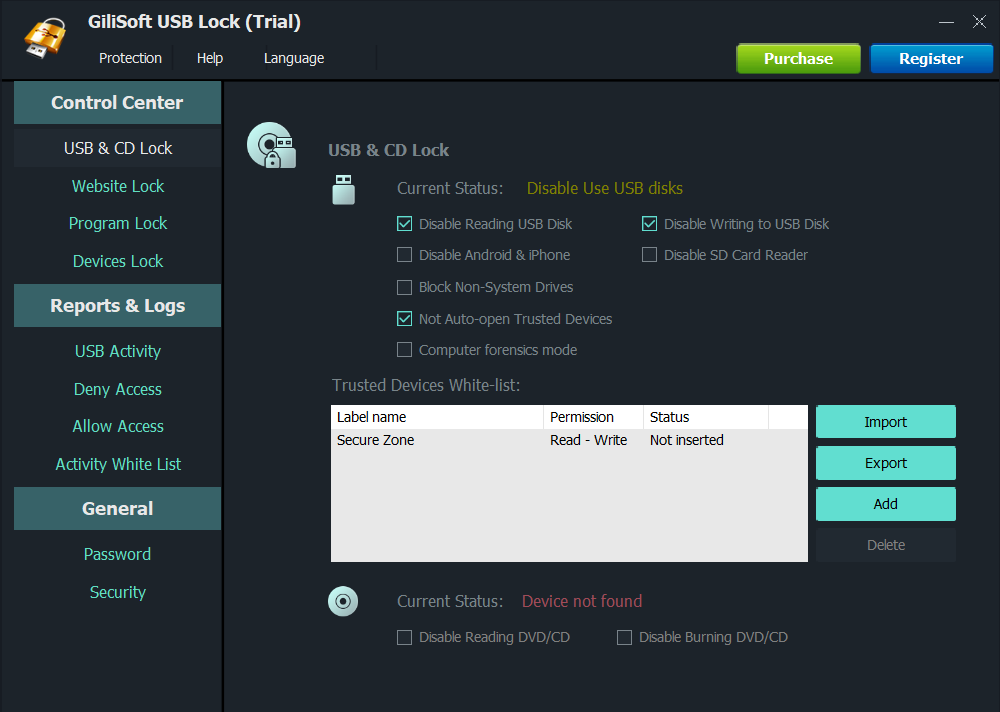
(I) Powerful Data Protection
GiliSoft USB Lock adopts advanced data leakage prevention technology, which can accurately lock the function of USB ports for network sharing, and at the same time, it does not affect the use of other normal USB devices such as mice, keyboards, and office U disks. It fundamentally eliminates the risk of data transmission through USB tethering and does not interfere with the daily operation of the computer. At the same time, the software can also set the DVD/CD burner to read – only to prevent data theft by burning optical discs.
(2I) Flexible Device Management
Users can easily create a trusted device whitelist through GiliSoft USB Lock. With just a few simple operations, necessary USB devices can be added to the whitelist to enable them to connect to the computer normally, while other unauthorized devices, including mobile phones, will be automatically blocked from connecting. This flexible management method not only meets the user’s needs for using necessary devices but also maximizes data security. The operation is convenient, and even non – professional users can easily get started. For example, enterprises can add specific U disks needed for office work to the whitelist, while employees’ personal mobile phones and other devices cannot access the company’s computers, effectively preventing internal data leakage.
(3) Comprehensive Activity Monitoring
The software provides complete reporting and logging functions, which can record the activities of USB devices in detail, including file operations on all USB disks connected to the computer, such as creating and deleting files. At the same time, it can also record the history of denied and allowed access as well as the active whitelist and other information. Through these records, users can clearly understand the usage of USB devices, and take timely measures to deal with any abnormalities, making the protection more proactive and accurate.
(4) Strong Self – Protection
GiliSoft USB Lock has a strong self – protection mode. Without the correct password, no one can uninstall the software. Users can also set it to stealth mode to further improve the security of the software. When someone enters the wrong password more than 5 times, the software will send an alarm notification to the user’s predefined email and temporarily prohibit unknown logins, effectively preventing others from maliciously cracking the software settings and ensuring that the software can always play a stable protective role.
To sum up, with its convenient operation, accurate protection and no side effects, GiliSoft USB Lock provides users with an efficient solution for disabling USB tethering and managing USB devices, helping users easily cope with data security challenges and ensuring comprehensive protection of computer data.

